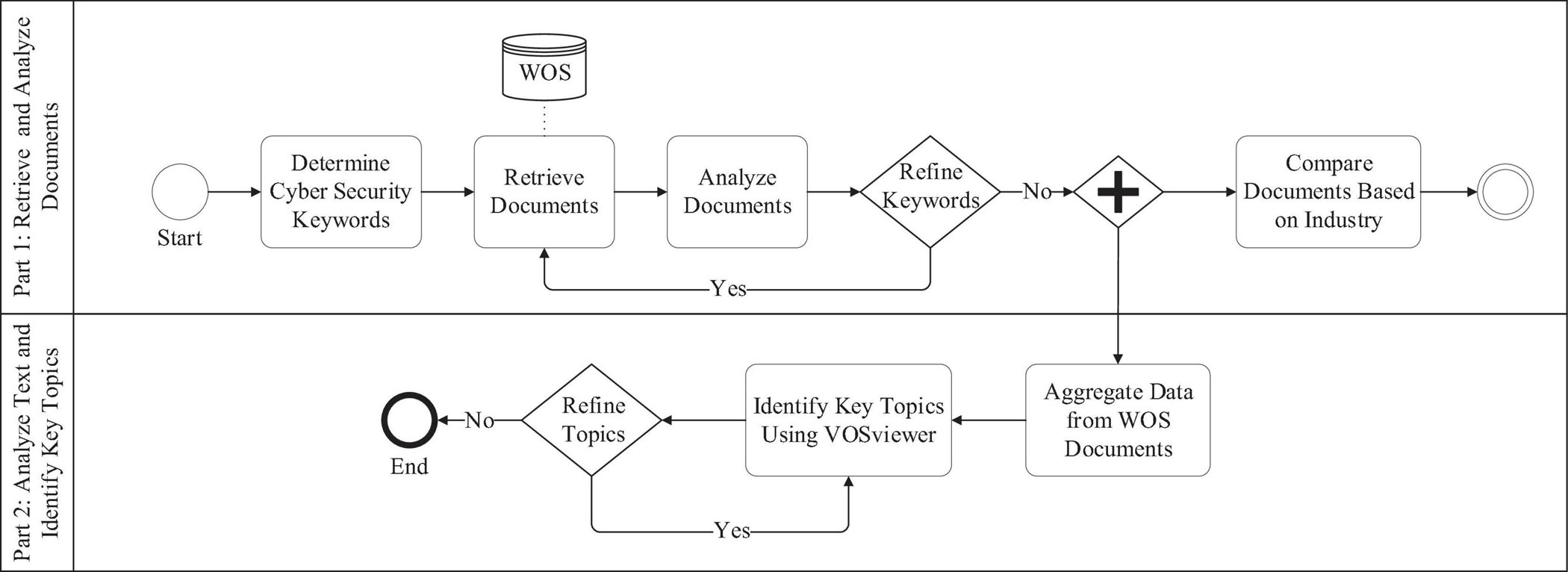
Figure 4 from Vulnerabilities and Countermeasures - A Survey on the Cyber Security Issues in the Transmission Subsystem of a Smart Grid | Semantic Scholar
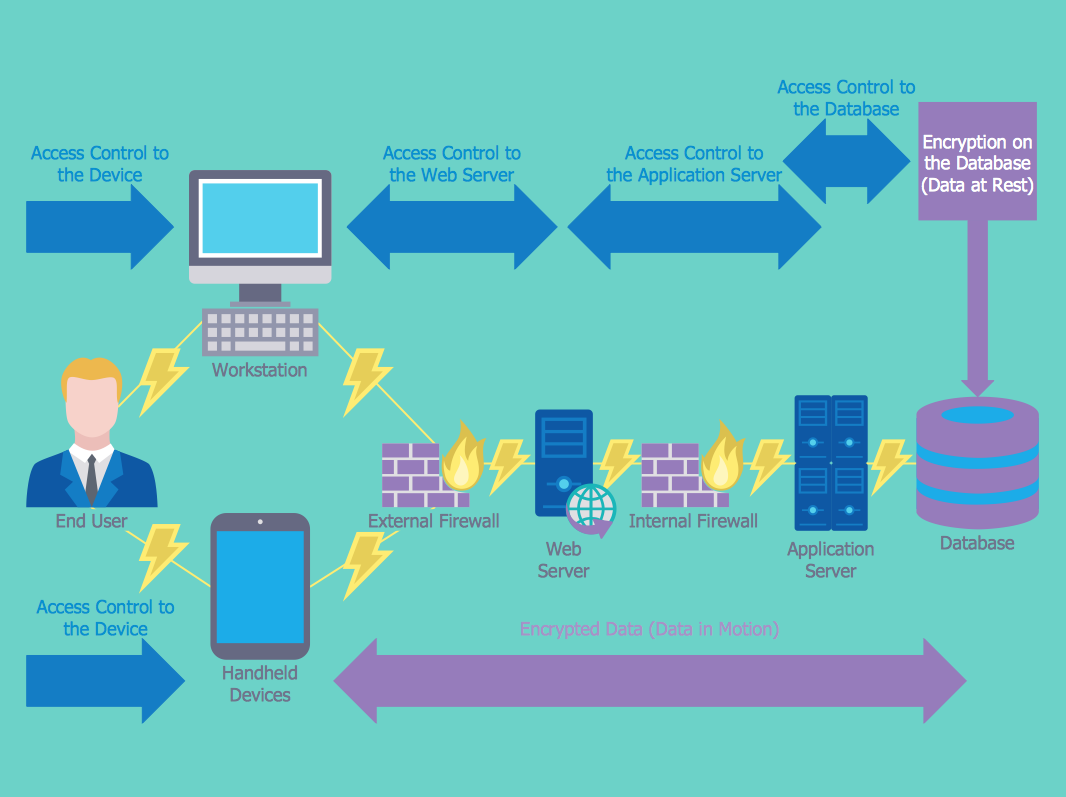
How to Create a Network Security Diagram Using ConceptDraw PRO | Network Security Diagrams | Recommended network architecture for BlackBerry SWS | Network Security Block Diagram With Working
Cyber Security Blockchain Ppt Powerpoint Presentation Professional Templates Cpb | PowerPoint Design Template | Sample Presentation PPT | Presentation Background Images

CyberSecurity Strategy - Best Practices by Industry | Cyber security, Cyber security technology, Cyber security awareness
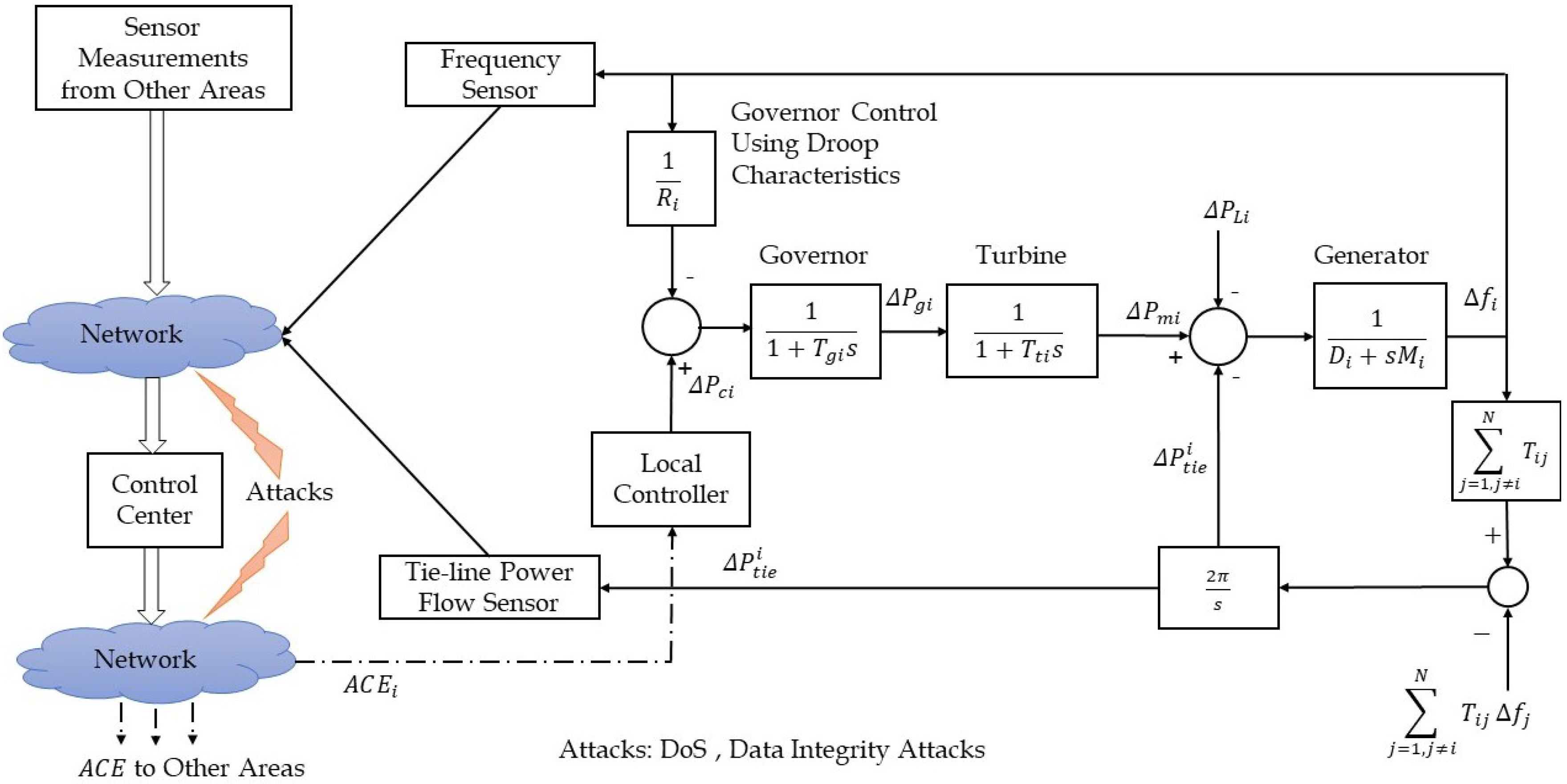
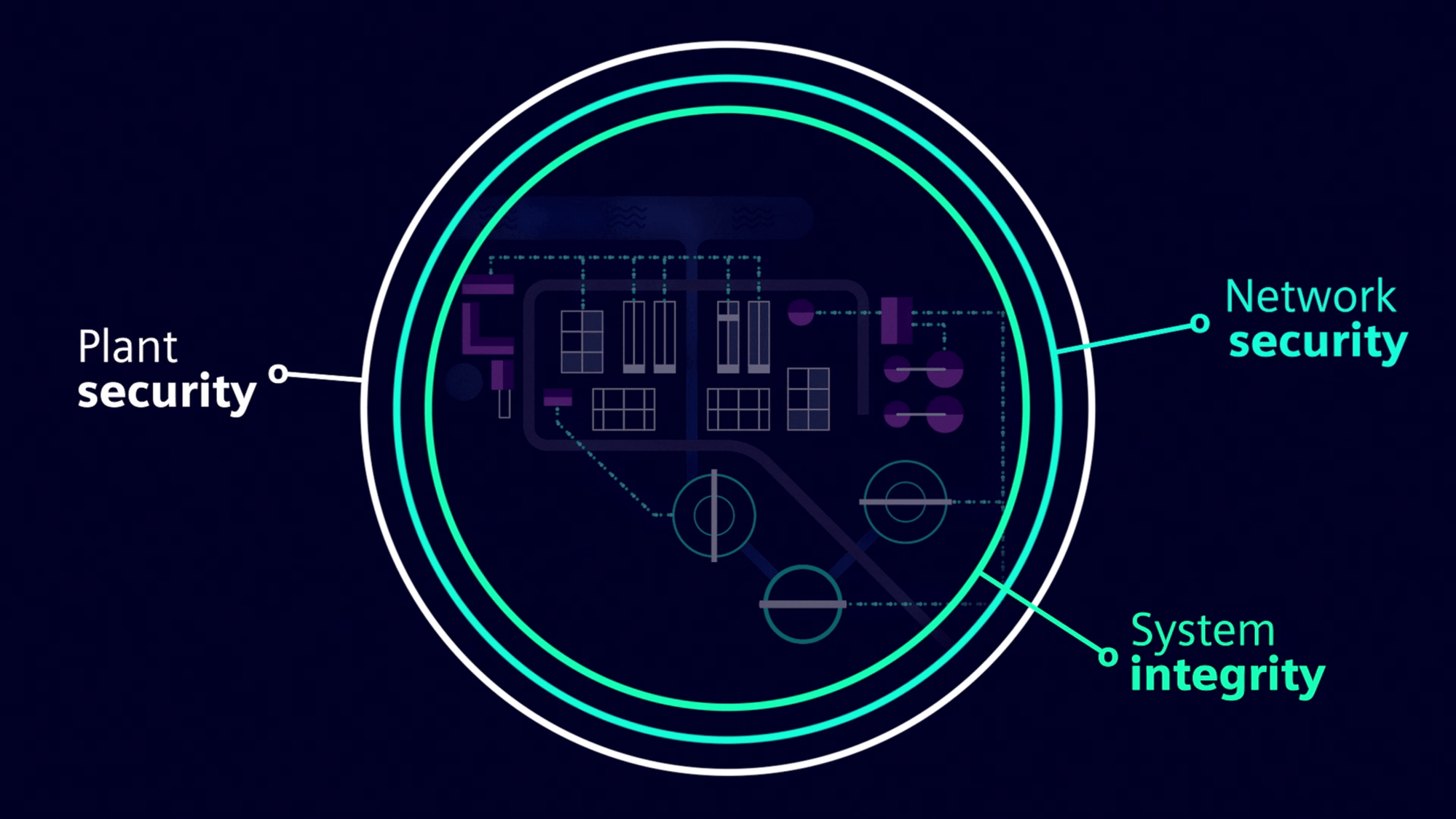
Energies | Free Full-Text | A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems

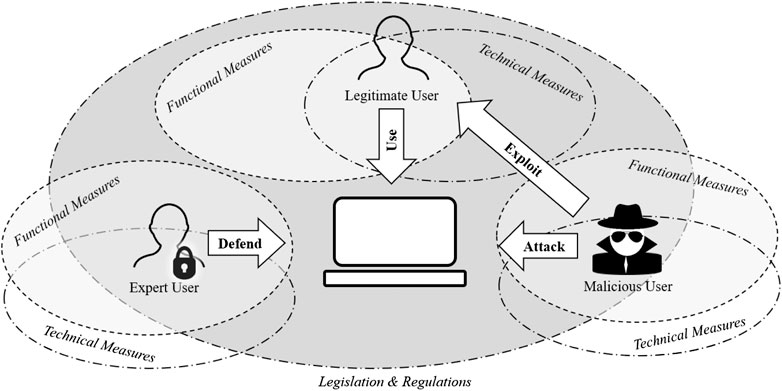
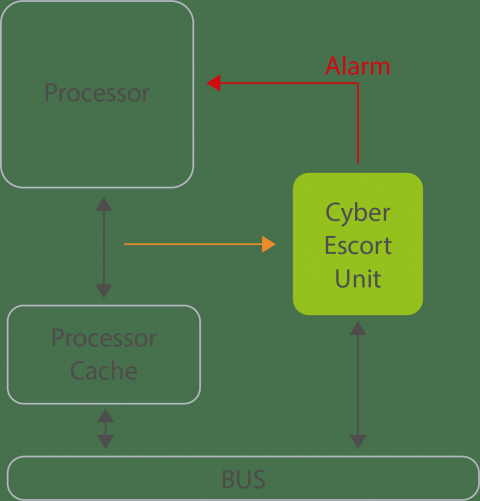
Figure 2 from Cyber security threat analysis and modeling of an unmanned aerial vehicle system | Semantic Scholar